Something we have talked about before is VMware vSphere NIC teaming. We started out simply, with an introduction, and talked about two of the easiest VMware load balancing algorithms to use: route based on originating virtual port and route based on physical NIC load. Now, I want to take some time to take a look at two of the more advanced VMware vSphere NIC teaming methods:
- Route Based on IP Hash
- Route Based on Source MAC Hash
Why Are These VMware NIC Teaming Methods More Advanced?
I am calling both of these more advanced, since they are a bit more complex in the way they work compared to some of the other VMware NIC teaming methods. That does not mean you should not use them, or they are bad. The NIC teaming method you choose depends on your unique requirements and the rest of your environment.
The Route Based on IP Hash Load Balancing Algorithm in VMware
I am starting with the route based on IP hash load balancing algorithm because it is the most complicated. Route based on IP hash requires additional configuration outside of your VMware vSphere environment. Because of this, it may not be the ideal choice for your environment, but it does have some advantages.
First, let’s take a look at the required external configuration required.
Physical Network Switch Configuration for Route Based on IP Hash
The use of this load balancing algorhtim requires configuration on your upstream physical network switches. If you are using a vSphere Standard switch, a static EtherChannel configuration is required. If you are using a vSphere Distributed switch, you have the ability to use LACP. If you are not a networking person, don’t worry. VMware has a very helpful KB that explains some of these concepts and provides a configuration example.
How Route Based on IP Hash Works
The name of this VMware load balancing algorithm tells you a lot about how it works. Let’s take a closer look at what actually happens to a packet when route based on IP hash is being used:
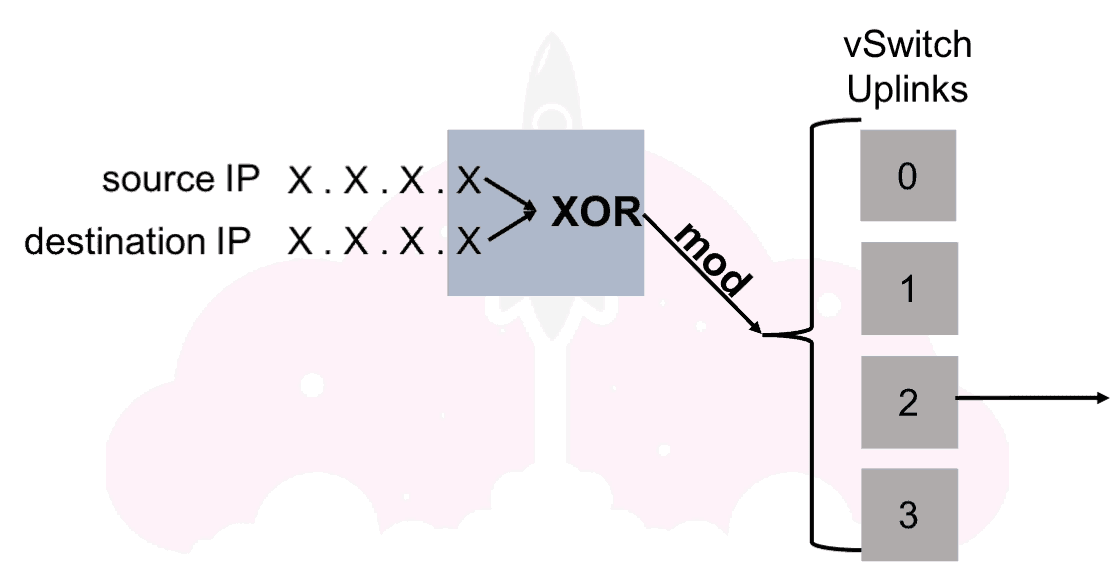
The hashing operation is done on the last octet of the source IP and the destination IP. The mathematical operation used to do this is called exclusive or or XOR. If you have ever taken a computer science class you may be cringing, and if you have not that is OK to. If you are really interested in how XOR works, there is a great Wikipedia entry here.
After the XOR, another calculation called modulo or mod is done between the result of XOR, and the number of NICs in the team. If you are not familiar with the modulo operation once again Wikipedia has a great explanation. Remember, there is a 0th NIC in the team, so the final result will always be something between 0 and N-1.
In this example, the XOR operation and the second calculation ended up with a result of 2, so the packet was sent out of vSwitch Uplink (or NIC) 2.
Benefits and Drawbacks of Route Based on IP Hash
Remember, these calculations are done for every packet sent from the virtual machine, so when traffic is being sent from multiple sources (such as a multi NIC VM) and to multiple destinations is where we will see the best load balancing.
Because these two mathematical operations are done on each and every packet each virtual machine sends, there is extra overhead associated with it. Is this realistically a problem with the powerful ESXi hosts of today? It could be in situations with a large number of virtual machines that require ultra high performance. It is always important to perform testing with these different VMware load balancing algorithms in your environment to determine what your results will be before production use.
You can find the official VMware documentation on the route based on IP hash load balancing method in the official vSphere Networking Guide.
The Route Based on Source MAC Hash Load Balancing Mechanism in VMware
The next VMware load balancing mechanism we are going to take a look at is route based on source MAC hash. After talking about route based on IP hash, this VMware load balancing method is a little easier to understand.
Similar to route based on IP hash, route based on source MAC hash calculates the uplink to be used for each packet.
Unlike route based on IP hash, route based on source MAC hash does not require any additional configuration outside of your VMware vSphere environment.
In this case the hashing algorithm once against uses the modulo or mod operation between the virtual machine’s MAC address and the number of uplinks in the NIC team to calculate which uplink should be used.
Benefits and Drawbacks of Route Based on Source MAC Hash
The benefits of route based on source MAC hash are similar to that of route based on IP hash. Since we are using the MAC address and number of uplinks in the vSwitch, the virtual machines that will benefit most from the use of those load balancing algorithm are those with multiple virtual NICs.
Since only one mathematical operation is done to determine the vSwitch uplink to be used, it does have slightly less overhead than route based on IP hash, but more than some of the other vSphere load balancing mechanisms.
[the_ad id=”2198″]
Summary of NIC Teaming in VMware vSphere
NIC teaming in VMware vSphere is all about providing protection against network failure and load balancing for our VMware vSphere environment. NIC teaming is the act of telling these vSwitch Uplinks, or the physical network ports in your VMware vSphere environment how to behave to provide these features.
We have covered these VMware load balancing mechanisms in detail. Here they are listed, with the links to each article that covers them. Be sure to read the Introduction to VMware NIC Teaming first!
- Route based on IP hash (this article)
- Route based on source MAC hash (this article)
- Route based on originating virtual port
- Route based on physical NIC load
- Use explicit failover order
Remember, it is always important to consider your project’s requirements when you are deciding how to configure NIC teaming in VMware. Testing settings before they go into production are always a good idea in order to ensure you are picking the best VMware load balancing method for your needs.

Melissa is an Independent Technology Analyst & Content Creator, focused on IT infrastructure and information security. She is a VMware Certified Design Expert (VCDX-236) and has spent her career focused on the full IT infrastructure stack.