I recently had the honor of being ransomware in the cloud, which was not totally unexpected. After all, one of my greatest complaints about the cloud (you can read more about why I hate the cloud here), is that people don’t design, architect, or secure it properly and my lab is no exception to that rule.
The good news is that I was ready to restore from backup in less than 7 minutes.
Here’s the details.
My Veeam Backup & Replication Server was Ransomwared
First of all, how is this for ironic? It was my Veeam Backup & Replication server that was theoretically crippled by ransomware. Oh no, what ever will I do? First things first, I nuked it from orbit, after I grabbed a few screenshots.
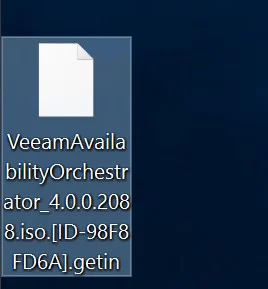
They got my Orchestrator ISO! How dare they!
I was very scared by the ransom note left on my sever and the aol e-mail address I was supposed to send bitcoins to. No, just kidding, I actually started laughing when I realized what happened.
First things first, I needed a new Backup & Replication server, which I just happened to have handy since I have Veeam Disaster Recovery Orchestrator.
Veeam Disaster Recovery Orchestrator’s Embedded VBR is Awesome
Here’s something that many people may not know. Veeam Disaster Recovery Orchestrator or (VDRO or simply Orchestrator) depending on my mood has an embedded version of Veeam Backup & Replication on it. It is fully functional, and does anything and everything a VBR server does.
That means I had a VBR server on standby. People are always asking me, oh no, what happens if I lose B&R? Well, you build another one really fast unless you have Orchestrator already :).
Add Object Storage Repository for Recovery
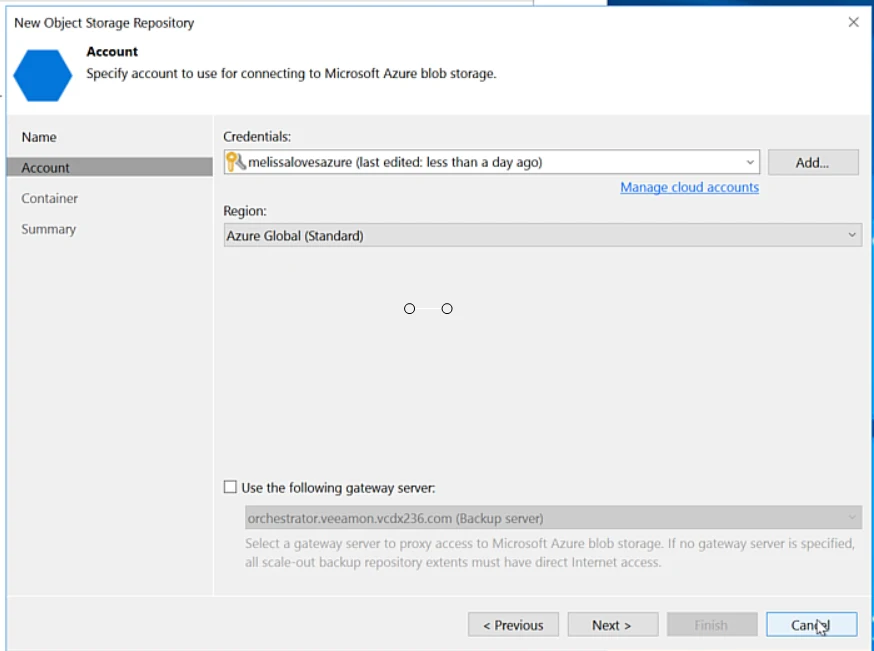
I launched the VBR console, my dearest friend, then I added my object storage repository where my backups were stored. This lab was designed to be trashed out at some point, to be re-deployed later. I was sending my backups to a SOBR leveraging Azure for my capacity tier, so my data was there.
Contrary to what this says, Melissa does not in fact love Azure. What slowed me down here actually was that I had to dig through the Azure portal to figure out my storage account key.
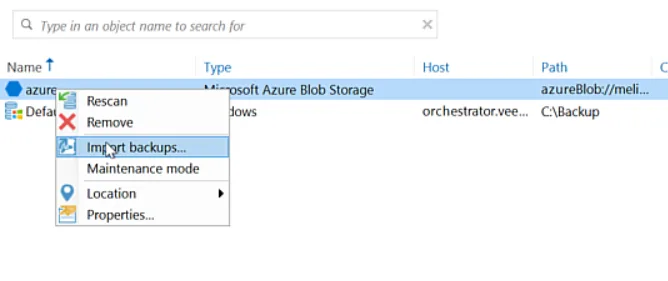
I added my repository, and imported my backups.
This was a pretty small environment so it didn’t take much time at all.
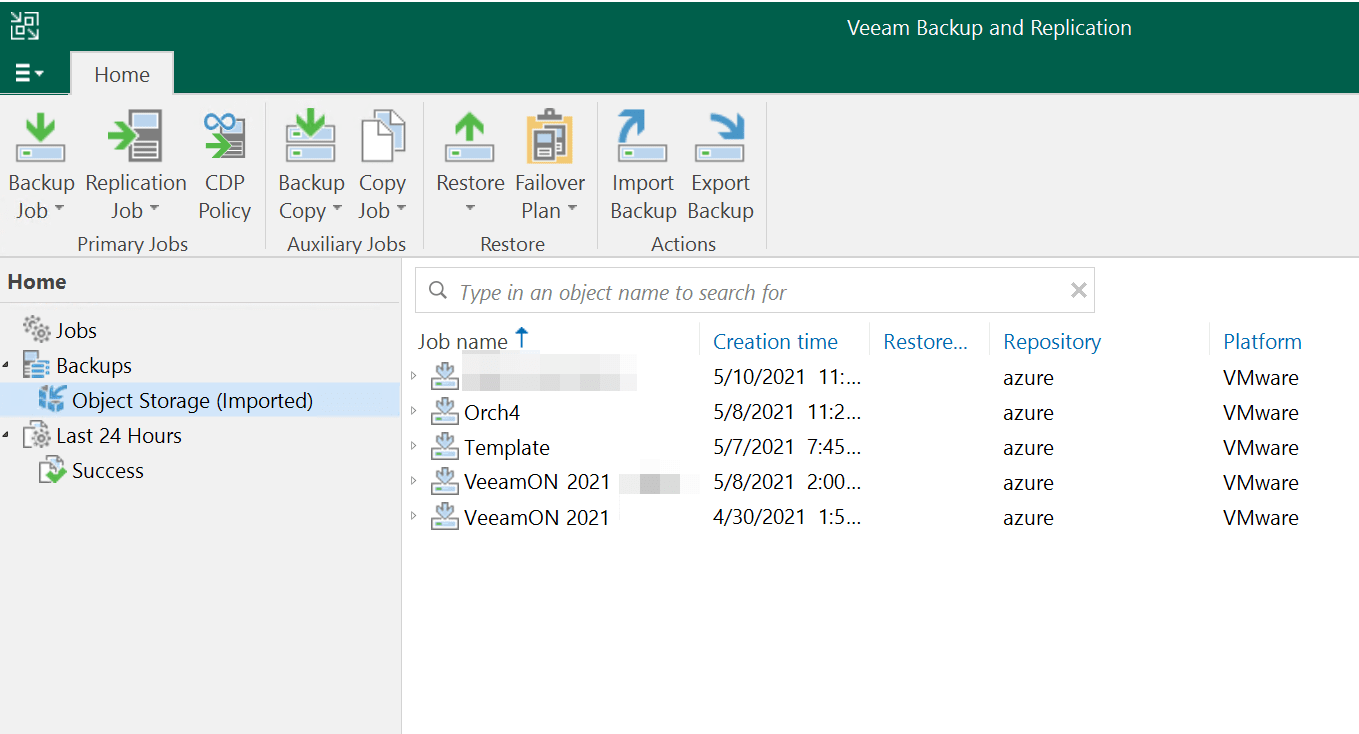
Here’s all of my jobs, and I can restore in whatever manner I please.
This whole process took less than 7 minutes, even with me fumbling around adding my backup repository, which is pretty good actually.
My Ransomware Recovery Strategy
The funny part of this is I didn’t actually have a ransomware recovery strategy for this environment because it was a lab. I happened to design it well enough that it was a breeze to recover because I basically built a disaster recovery strategy for it to re-use some of the components in the future.
It took me 7 minutes to get ready to restore my VMs which honestly was pretty great considering my recovery strategy was an afterthought.
Here’s why I could recover so quickly:
- I had a copy of my data in object storage in the cloud so who cares if my on prem repo was hosed
- I had a Backup & Replication server ready to go in my recovery site via Veeam Disaster Recovery Orchestrator
- Veeam’s data format is ultra portable. I literally do not ever care what happens to my Backup & Replication server, because I can just connect a new one to my repository and off I go.
This is part of the reason I’ve been yelling about disaster recovery for the last several years. Ransomware? Yeah, that is kind of a disaster. If you have a proper disaster recovery plan, you can leverage that for ransomware recovery.
Remember, it isn’t if you get ransomwared, but when :).

Melissa is an Independent Technology Analyst & Content Creator, focused on IT infrastructure and information security. She is a VMware Certified Design Expert (VCDX-236) and has spent her career focused on the full IT infrastructure stack.