The NSA has released specific guidance to system administrators in January of 2021. The recommendation is to eliminate obsolete Transport Layer Security (TLS) configurations. This is a very important reccomndation that every organization should take under advisement. Let’s take closer look at TLS and why this recommendation was made.
What is transport layer security (TLS)?
Transport Layer Security (TLS) is a protocol used to secure communications over computer networks. It was created with the purpose of being an improvement to Secure Socket Layer (SSL). TLS provides strong encryption, authentication, and integrity checking for data transmitted over the network, helping to protect against malicious third-party interception and modification of data.
More on the NSA TLS recommendations
The National Security Agency (NSA) recently urged system administrators to replace obsolete TLS protocols, such as SSLv2 and SSLv3, with more up-to-date versions in order to protect the privacy and security of their networks. Upgrading existing systems is critical to ensuring that sensitive information remains safe and secure. Additionally, using the latest version of TLS is important for interoperability and compatibility with other systems.
In the context of the NSA guidance, when the guidance mentions TLS, it implies all versions of TLS as well as SSL versions.
If you’re responsible for maintaining a system, it’s important to periodically review your security settings and ensure that all components are compliant with the most recent standards. Upgrading to new TLS protocols can be done quickly and easily, and can help protect your system from potential attacks.
It’s also important to remember that security is an ongoing process, and that regular testing and updates are essential to maintaining a secure network. Taking the time to upgrade your TLS protocols now can help keep your system safe for years to come.
Why this guidance is so strong
This guidance from the NSA is very strong. They mark the following specific recommendations:
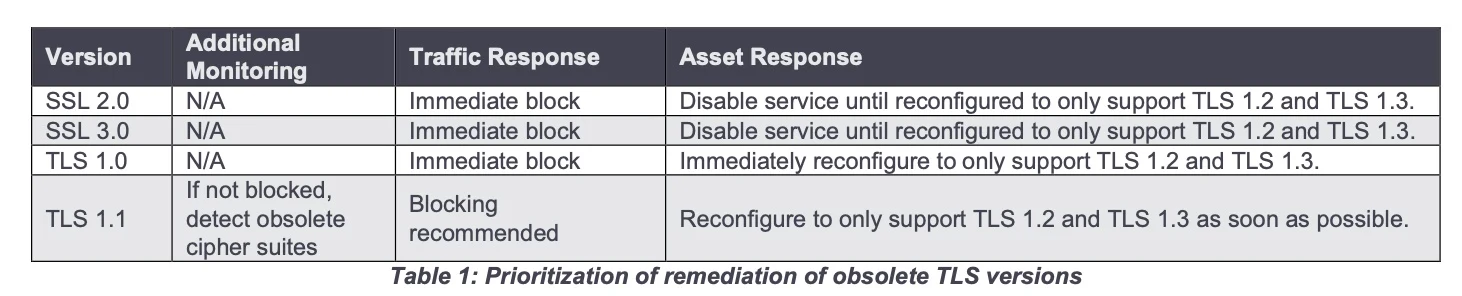
IMMEDIATELY BLOCK: TLS 1.0, SSL 2.0, SSL 3.0
BLOCKING RECCOMENDED: TLS 1.1
TLS versions used should be TLS 1.2 and 1.3.
This is because there are vulnerabilities with the earlier versions of SSL and TLS. When we have vulnerabilities in our environments with known exploits, the risk of an attack increases significantly.
How to mitigate obsolete TLS
There is information available on how to mitigate obsolete TLS from the NSA which you can find here.
The first step in mitigation is scanning your environment to find where obsolete versions of TLS are being used. This is especially important because it could be utilized on systems and current administrators may not even realize it if the people who designed and built the systems have moved on to other roles or organizations.
Once usage has been identified, then improvements can be made and more secure versions can be implemented. This may require multiple changes to the environment. While this is a critical issue, care still must be taken to follow proper change management protocols. After changes are made, systems should be observed further to ensure they are working as expected. It is also important to have a rollback plan for these changes should they go wrong.
Click here to review the recommendations from the NSA.
Be sure to check out some of the latest cybersecurity news from vMiss.net.

Melissa is an Independent Technology Analyst & Content Creator, focused on IT infrastructure and information security. She is a VMware Certified Design Expert (VCDX-236) and has spent her career focused on the full IT infrastructure stack.
