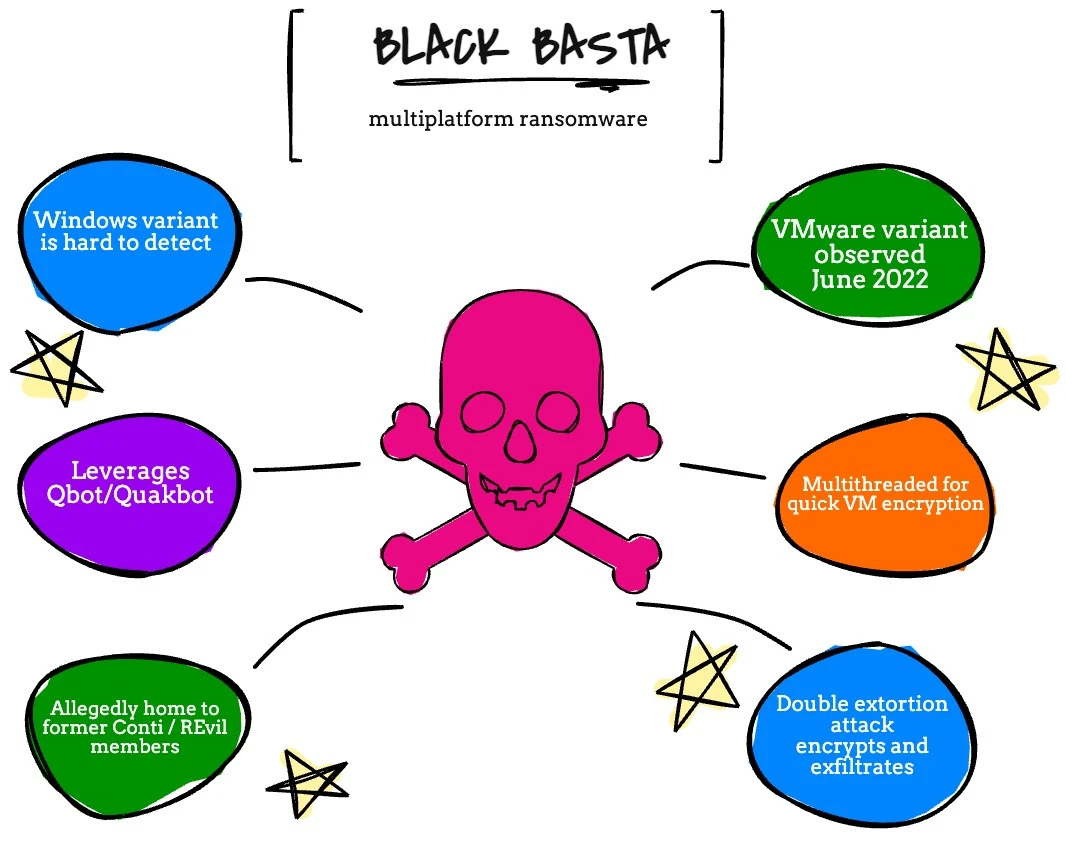
Black Basta Rasnsomware is a multiplatform ransomware strain targeting Windows, Linux, and VMware ESXi. Black Basta is an interesting ransomware organization, as it is believed that there are former Conti and REvil members participating in it. If that doesn’t sound like a disaster waiting to happen, I don’t know what is.
A Closer Look at Black Basta Ransomware
Besides allegedly having quite an interesting pedigree when looking at who is participating in these activities, Black Basta ransomware started gaining traction in May of 2022.
What’s interesting about Black Basta to me is that they posted on forums actively seeking corporate network access credentials. This is probably one of the reasons they were able to attack a number of organizations qucikly.
This is almost a reverse Ransomware as a Service (RaaS) model, but if you think about it makes a lot of business sense. After all, the hardest part (which doesn’t seem to be that hard in many cases) is getting in.
Like most ransomware groups out there, Black Basta performs a double extortion attack. They encrypt and exfiltrate data, to really make sure their victims pay.
More Interesting Things about Black Basta
Black Basta really has done some interesting things, which makes me think that the Conti and REvil relationship is true. For example, they leveraged Qbot/Quakbot in a recent attack, which helps with their initial reconnaissance and allows them to collect more data quickly to wreak as much havoc as possible. As part of the initial compromise, Black Basta is also adept at avoiding detection.
In this context, we’re talking about Windows, but remember, Black Basta is a multiplatform ransomware group.
In June, Black Basta was first observed targeting ESXi. What’s really interesting is that it also uses multhreadting to make it as fast as possible when it comes to encrypting. Remember, ESXi is a target because it is easy to cause a ton of damage and impact very quickly.
Here is something fundamental to know about VMware in order to understand the impact of VMware ransomware.
In VMware, a virtual machine is simply stored as a file. This file is on something called a datastore. The datastore is connected to every host in the VMware ESXi cluster, which means a single host can see every VM in the entire cluster.
VMware hosts are designed to run multiple virtual machines, which means they have ample CPU and Memory. That CPU power is what is used for encryption, which makes it even more quick and dangerous. In VMware ransomware, the files that make up the virtual machines are encrypted by leveraging the CPU power of the VMware host.
Black Basta is an interesting group, because of their quick rise in destruction, and how fast they have innovated their software. From April to June, they increased their number of victims quickly, and then got into the VMware ransomware game to cause maximum destruction.
Looking for more insight on the VMware ransomware threat? Don’t miss these awesome strains.
Stay tuned for more coverage on what you need to know to be able to defend against a ransomware attack, and recover VMware vSphere from ransomware.

Melissa is an Independent Technology Analyst & Content Creator, focused on IT infrastructure and information security. She is a VMware Certified Design Expert (VCDX-236) and has spent her career focused on the full IT infrastructure stack.