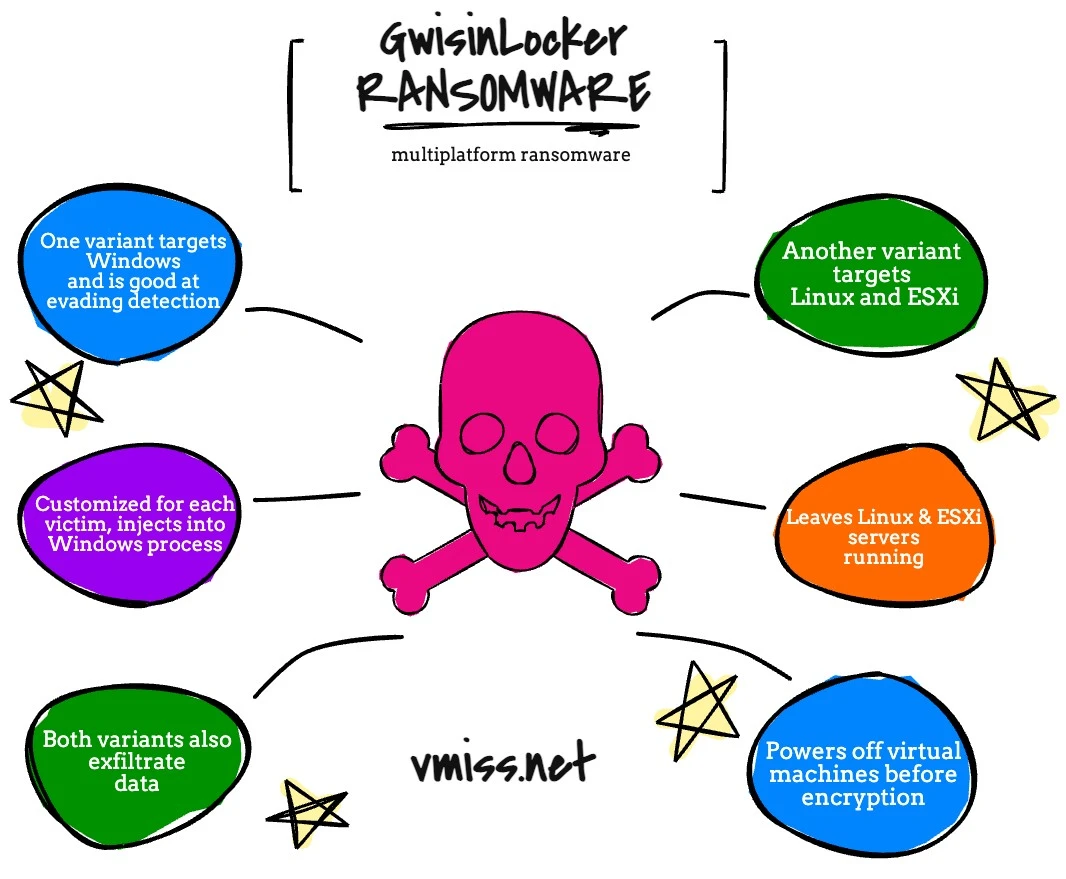
GwisinLocker is a new piece of mutiplatform ransomware with a twist. It is a linux variant of ransomware targeting Linux machines and ESXi directly. While it does end up encrypting Windows VMs, it does not target the Windows OS specifically to exploit it;.
This particular ransomware strain is very interesting, because it is targeting victims located in South Korea. I’ve noticed a bit of a shift in specific strains getting a bit more political, as well as targeting government organizations. With many cyber attacks the motive really needs to be examined to see if there are any trends that can help us understand these threats better.
Of course, at the end of the day, the motivation is getting victims to pay, above anything else.
This ransomware strain is from a threat group known as Gwisin, which was first observed towards the end of 2021.
Let’s take a closer look at this one, because there are two main focuses: the Windows variant and the Linux Variant. There was information related on both variants very recently, which makes it a great candidate to dive deeper on the concept of multiplatform ransomware.
GwisinLocker Windows Ransomware
The Windows strain of GwisinLocker was discovered and reported on by Ahnlab, and I highly encourage you to read the research here.
The most interesting thing about this strain is that it operates by being injected into a Windows process, which is customized for each victim. This makes it more difficult to detect, and it is clear these threat actors are taking a very hands on approach for maximum destruction. It is observed that this strain is very good at avoiding detection by security software.
Gwisin also exfiltrates data, another way to try and force the victims to pay ransom. Of course, with large numbers of Windows machines in almost any environment, Windows based ransomware is probably the most popular, but is it the most profitable?
GwisinLocker Ransomware – Linux and ESXi
The Linux version of GwisinLocker was first discovered by ReversingLabs researchers. I highly encourage you to read their direct report here, because I’m seeing a lot of weird stuff out there about this one, especially with the two variants that were observed. This ransomware targets Linux and ESXi.
When we talk about the Linux variant, GwisinLocker is a very interesting piece of multiplatform ransomware, since it is focusing on Linux and accessing Windows via ESXi, not going after the Windows machines directly.
A Windows VM on ESXi being encrypted by this ransomware is not the same as the Windows variant – these are two very different ransomware strains by the same threat actor.
GwisinLocker shuts down the VMs before encrypting them. Remember, when we’re talking about ESXi, at the end of the day, each VM is nothing more than a collection of files on a disk someplace. When the VM is off, it is just a matter of encrypting those files, versus the Windows based ransomware which is injecting itself into processes.
This ransomware strain also ensures it does not encrypt the files that are vital to the operation of the Linux and Windows operating system, it wants your severs to be bootable and operational, but not actually usable. This could also help them to evade detection.
In this case, with the Linux variant, each attack is customized for each victim, just like with the Windows version, and data is also exfiltrated.
GwisinLocker Targets
Both research firms noted that attacks at this time are towards organizations in the industrial and pharmaceutical industries although BleepingComputer mentions they are aware of a healthcare clinic that was also targeted. This is going to be an interesting one to follow as attacks continue to ramp up.
The Dangers of Multiplatform Ransomware
GwisinLocker is just another illustration of the dangers of multiplatform ransomware. In order to be sure we are able to recover encrypted machines later, we need to make sure we are protecting our assets today, whether they be physical or virtual, and no matter what operating system they are running.
Check out my favorite ransomware defense tips!
Be sure to take a look at my living document, recovering vSphere ESXi from ransomware, and be sure to let me know if you have any questions.

Melissa is an Independent Technology Analyst & Content Creator, focused on IT infrastructure and information security. She is a VMware Certified Design Expert (VCDX-236) and has spent her career focused on the full IT infrastructure stack.
