While responding to a security advisory may not be a daily occurrence in a VMware vSphere environment, the occasion still arises when a prompt response is needed. This will depend on a number of different things, like how critical the threat is, and what processes your organization may already have in place. If you do not have a security advisory response plan for your VMware vSphere environment, now is the time to create one.
The latest VMware Security Advisory is VMSA-2022-0021.
Need instructions on how to patch VMware?
How to Patch a VMware ESXi Host Using Update Manager
How to Upgrade the vCenter Server Appliance to vSphere 6.7 U3
For some reason, many are hesitant to reach out to their organization’s information security team. Many see them as the enemy since a conversation with them usually results in more work for an administrator. The fact is your information security team is there to help you protect your environment and your data. Here are a couple things to think about as a VMware vSphere administrator when a threat arises.
Here for VMSA-2019-0008? Aka Zombieload/RIDL/Fallout? Read on for some tips to help, don’t worry, VMware has you covered! Patches were available on day 0!
Ready to reach out to to your friendly neighborhood information security colleagues and have a conversation about your VMware vSphere environment? Are you just starting to think about security and how it relates to VMware vSphere? Has a new vSphere vulnerability emerged? Here are some things to help get you in a more secure mindset.
Pay Attention Key VMware Security Advisories
In the event of a security advisory, you will be notified by VMware. You can also follow VMware Security Advisory and Response on Twitter for the latest advisories. Is this your first time looking at a security advisory? Let’s take a look at a recent one, and see if we can make sense of it together. This advisory is named VMSA-2018-0002, which means it is the second VMware Security Advisory of 2018.
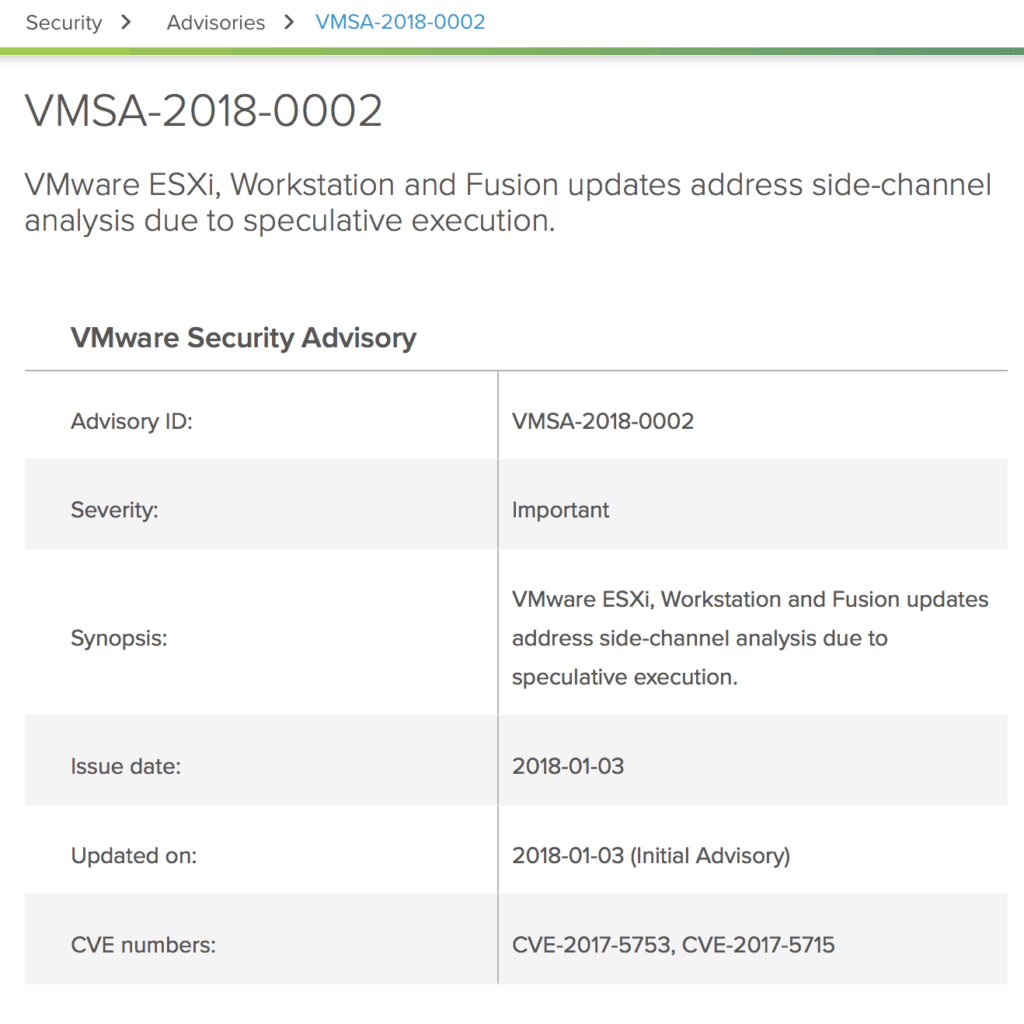
(NOTE: This is a screen shot taken from VMware’s Security Advisory site for illustrative purposes. Always check the security advisory for the latest information, in this case, the link is here: VMSA-2018-0002. Do not save security advisories to your computer for later use, always check the active link for the latest information.)
First, let’s look at the severity. In this case it is important, which means we need to read and understand it, and start thinking about how we can address it in our environments. If this advisory was critical, like VMSA-2018-0001, it means we need to act on it as soon as possible if our environment can be compromised by it.
Next, you will see information on the dates that the advisory was announced, and when it may have been updated.
Then, you will see the CVE number of the advisory. CVE stands for Common Vulnerabilities and Exposures, and it is a way to consistently track a vulnerability. While each vendor will release their own security advisories, they will all reference the common CVE number. You can find out more about CVEs here.
Next, you can read on to learn more about the specific threat, and what VMware products are impacted by it. Now that we understand more about what an advisory is and what information it gives us, what do we do now?
Plan Your Response to a VMware Security Advisory
Your response will depend on a number of things, such as how many of your hosts are impacted, the business applications they run, and the severity of the treat. This is where you should be talking to your information security team to understand the wider impact of the security advisory.
In some cases, the decision may be made to wait before taking any action. In other cases, the decision may be to patch immediately. Whatever the case is, it is important to have processes in place.
For example, if the decision is to wait before acting, part of your process may be to monitor the security advisory for changes, and re-assess after any updates. If the decision is to patch, you may decide to patch in your regular maintenance window, or you may need to request an emergency maintenance window.
A Word On Patching VMware vSphere
When there is a critical advisory, your fist instinct may be to patch your environment as soon as possible. While this is great from a security perspective, it is important to ensure the rest of your environment is not broken as the result of a patch.
This includes checking the VMware compatibility guide (matrix) for the new version of ESXi you may be upgrading or patching to and the things that interact with your vSphere environment such as your hardware, storage, and backup software. Don’t forget, when it comes to patching your environment, Update Manager is built into VCSA, and easy to use.
Need to patch the VCSA?
How to Upgrade the vCenter Server Appliance to vSphere 6.7 U3 shows you how to update the VCSA through the VAMI.
Need to apply a critical patch to ESXi?
- Check the VMware compatibility guide / VMware interoperability matrix
- Use VMware vSphere Update Manager to patch or upgrade ESXi. Simply follow these guides, and simple select the desired patch when creating a new baseline.
Even in the event of a critical patch it is important to maintain standard operating procedures, which usually involve testing the patch in development or test environments before moving it to production. This can of course be done on an accelerated schedule provided you have the buy in from your management team. In this case, the information security team may be able to help you communicate to management in the event a critical vulnerability requires immediate action.
But What About My VMs?
Usually, you virtual machines will be covered by their respective operating system operations team. For example, in the event of a Windows vulnerability, the windows operations team will often be the ones remediating the threat. As a VMware administrator, it is also important to have an understanding who is responsible for the workload being hosted in your environment.
It is important to confirm what teams have operational responsibility for the virtual machines in your environment, and ask them to review their information security procedures with you. If they do not have any, this is another opportunity to reach out to your friendly neighborhood information security team. They will not bite, I promise.
Practice Your VMware vSphere Security Advisory Response or VMware vSphere Incident Response
You know what they say, practice makes perfect! Make sure to practice how you would respond to a VMware vSphere Security Advisory. There is nothing wrong with taking an hour to sit around the table with the team to talk through how you would respond to a VMware Security Advisory. Here are two ideas to get you started:
- Respond to a VMware Security Advisory that impacts ESXi hosts
- Respond to a VMware Security Advisory that impacts virtual machines
The Next Step, Practice VMware vSphere Incident Response
After you have practiced responding to a security advisory, you have one more thing to begin to think of and practice responding to. Next, think about how you would respond to a VMware vSphere Security Incident. The big difference between a Security Advisory and a Security Incident is that a Security Advisory advises you something may happen, and with a Security Incident, it has already happened!
It is important to think of your VMware vSphere Security response in a the same way you thought about your response to an advisory, but you may want to go to an extra step and think about if your response would be different based on the virtual machines running on an compromised ESXi host, or based on the virtual machines compromised in general.
These are just a few things to think about as a VMware vSphere administrator in today’s world. Becoming familiar with security processes and procedures now will help you act swiftly and confidently in the event action is required to protect your VMware vSphere environment against a threat.

Melissa is an Independent Technology Analyst & Content Creator, focused on IT infrastructure and information security. She is a VMware Certified Design Expert (VCDX-236) and has spent her career focused on the full IT infrastructure stack.
