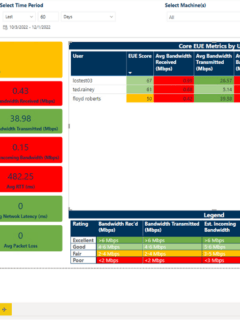
Recently I spent some time reviewing the ESI Benchmark Report from Hornet security and found some valuable insights. Also, as a long-time practitioner deploying email infrastructure and including deploying methods of phishing prevention, my interest in this topic and its evolution is still top of mind. The other pinnacle consideration here for your enterprises is that phishing attacks …
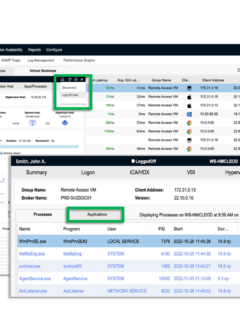
Virtual Desktop Infrastructure (VDI) is a popular solution for organizations seeking to provide their employees with secure and flexible access to their corporate desktops and applications. VMware Horizon is one of the most popular VDI products on the market, used by many different types of organizations, especially in the healthcare area. Like with any technology, issues …
Monitoring your enterprise end-user computing infrastructure is critical to ensuring systems are online and for proactive troubleshooting. Having the unique ability to engage in on-demand remediation of identified problems from within your monitoring solutions, gain insights into the user experience through a scorecard, intelligent sorting by active directory OU, and monitoring of both Citrix and …
Cyberattacks are a daily challenge and it’s critical to make sure that our users are responding to email related attacks appropriately. Having a service that will not only train the user on what email messages look like that host enterprise threats the ability to test them is important as well. While we may have email …
If you work in a technology role, then it won’t be any surprise to you when I say organizations have pivoted from specialist IT job functions, such as Citrix only roles, to making sure the infrastructure team can support many workloads. The adoption of cloud technologies has also created support for this approach because our …
Email is a primary way that security threats enter any organization, and then add the human element of mistakes and inadvertent misuse causing 82% of breaches and organizations may have an impossible time keeping vulnerabilities out of their users mailboxes. We often hear that it is not IF we will have an attack on our …