Email is a primary way that security threats enter any organization, and then add the human element of mistakes and inadvertent misuse causing 82% of breaches and organizations may have an impossible time keeping vulnerabilities out of their users mailboxes. We often hear that it is not IF we will have an attack on our enterprise, but it’s more of a matter of WHEN. While email is only one of the entry points for security threats, it’s a significant one. Today, let’s take a closer look at how Hornetsecurity 365 Total Protection Enterprise can help you keep security risks out of your user’s mailboxes.
So, what is the risk, really?
Email is a simple way for security threats to enter and organization. Email messages can contain attachments or URL links with viruses, malware, etc embedded in the email message that can execute and be planted on the server or computer in use. However, the even larger risk are the phishing emails that look legit, but really aren’t. Misinterpreting the contents of one of these emails can take a person down a path that could have them entering passwords, phone numbers and even their social security number. In some cases, the perpetrator is asking for gift cards and even money wire transfers. The messages that our enterprise users engage with look so real it’s almost too much to ask to of our users to put the risk on them. So why are we letting these messages get to our users when there are email filtering tools available that we can deploy that help filter out the chaos leaving the end user to focus on one thing…their job. So, let’s look at one of the product options available today.
Hornetsecurity 365 Total Protection Enterprise
Setting up 365 Total Protection Enterprise was straight forward with a brand new M365 tenant. Here are the high-level steps:
- Setup is primarily wizard driven and makes the security changes you need within your tenant.
- Beyond that you will need to make some DNS changes: Update your MX record(s), SPF record, and if you are using DMARC/DKIM you will also need to make some adjustments with that as well.
- Once setup the product will be able to scan your email before it enters your enterprise users.
To check on progress with what is being blocked or allowed through to your users you will need to login to the Hornetsecurity Control Panel and the URL for this is provided during the setup process. time goes by it’s easy to see what is happening, the types of messages, threats and what is being completely rejected.
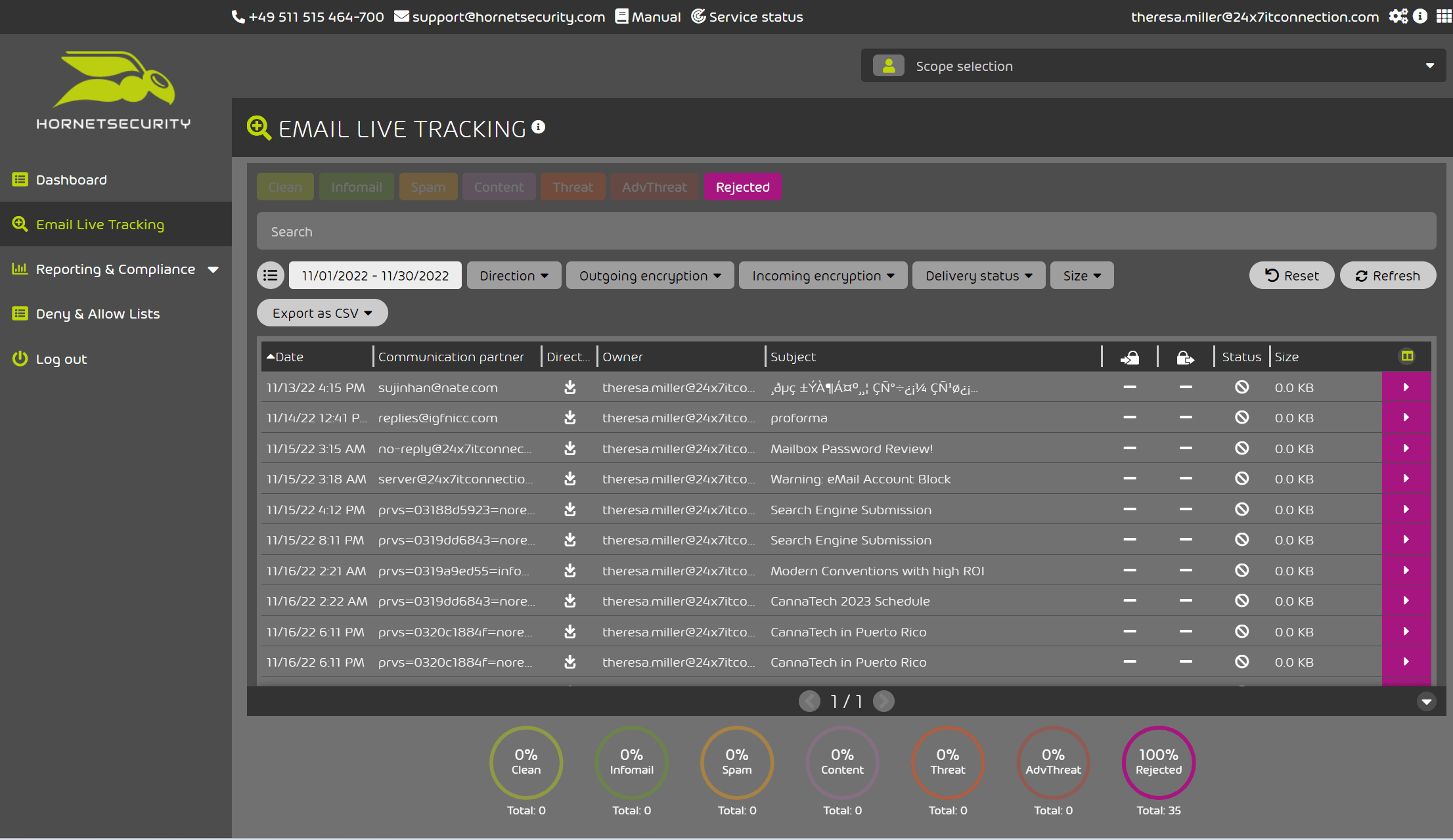
See in Figure 1 below the categories and at the bottom of the image note the percentages of each type, but I am personally most interested in what is being rejected.
Figure 1
In Figure 2 below I have filtered by “Rejected” only and at a glance completely agree with the tool’s decisions.
Figure 2
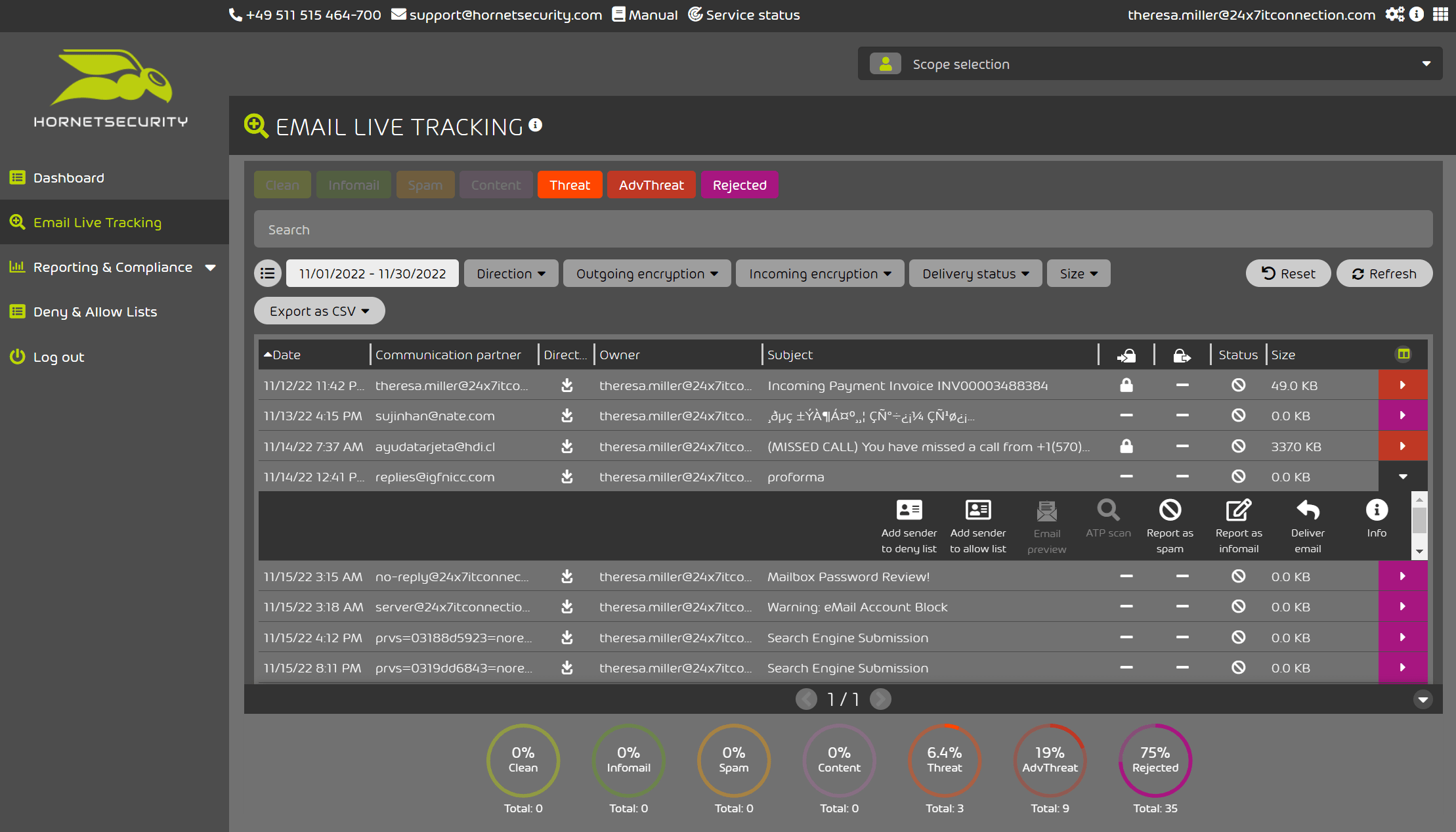
In Figure 3 below we can see that I am now filtered by “Threat”, “Adv Threat” and “Rejected”. It’s easy to review the threat message and just below it I can take additional actions such as “Add to Sender Deny or Allow List”, “Report as Spam”, “Report as InfoMail”, or even “Deliver” if I find that there was a false positive at hand or if you would prefer to do additional analysis with a fully formed email message.
Figure 3
Upon review I found I wasn’t receiving any malicious emails and Hornetsecurity 365 Total Protection Enterprise was accurately classifying and rejecting messages as I would expect.
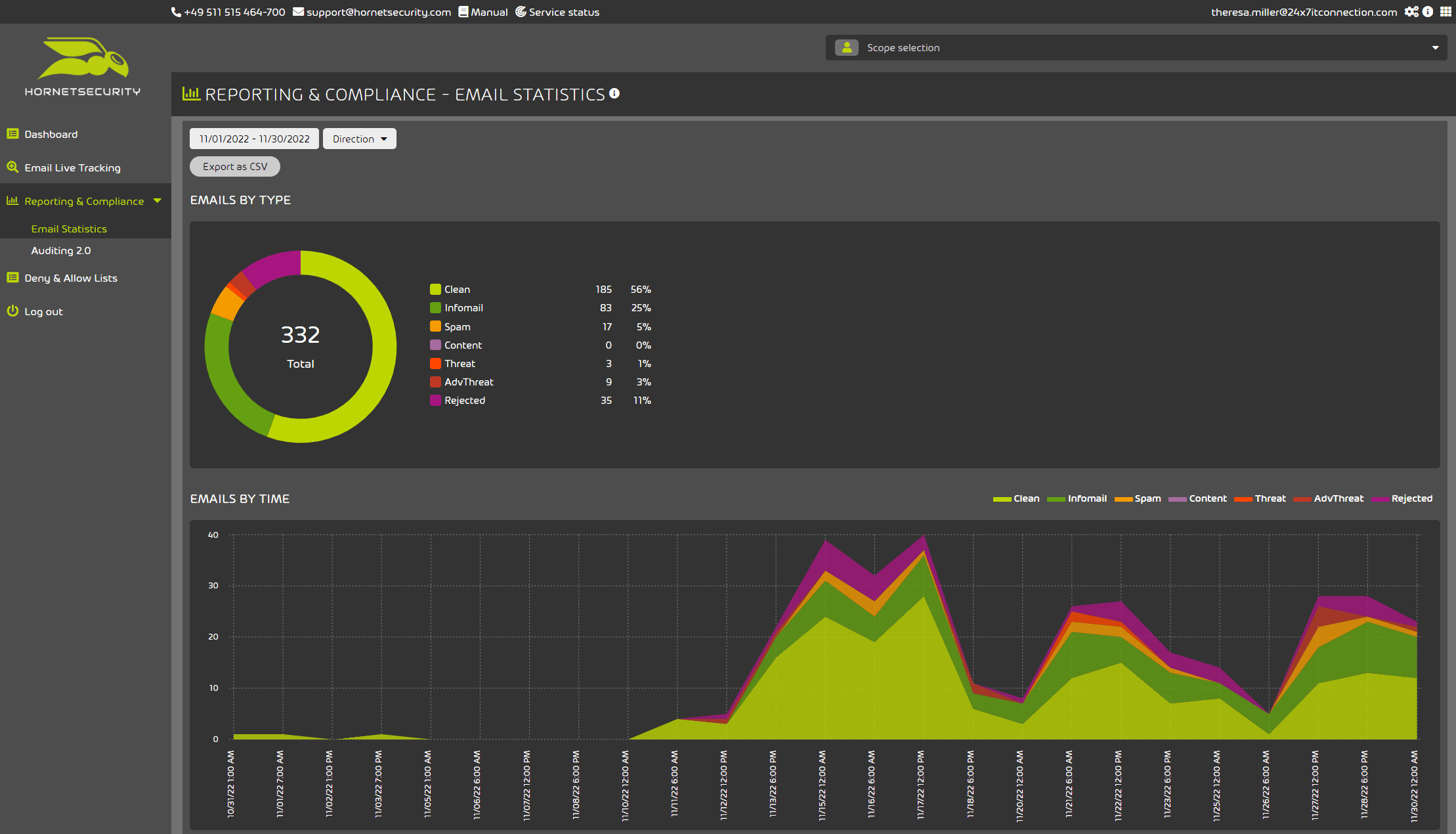
Other information within this tool that are helpful to have starts with the Email Statistics Reports shown in Figure 4 in the Reporting and Compliance section acts as a quick summary of how many messages have been reviewed and broken down into their detection categories.
Figure 4
Concluding Thoughts
With the evolving risk of threats entering organizations through email, it is imperative to have a solution that will scan your email messages as they enter your organization. This solution deploys in a simple fashion and effectively provides a level of email threat detection and rejection that will help prevent email vulnerabilities from making it to your enterprise users ensuring they can focus on doing their jobs instead of focusing on avoiding the latest phishing or malware attempt through email.
This post is sponsored by Hornetsecurity.
Theresa Miller is an IT professional that has been working as a technical expert in IT for over 25 years and has her MBA. She has been uniquely industry recognized as a Microsoft MVP and VMware vExpert. Her areas of expertise are in Cloud, Hybrid-cloud, Office 365, VMware and Citrix. She previously founded https://24x7itconnection.com and can be found on Twitter as @24x7itconnect.